Securing APIs in multi-cloud setups is complex but critical. Businesses rely on APIs to connect systems, and as they expand across AWS, Azure, and GCP, security challenges grow. Each cloud provider has different protocols, and managing diverse API types (REST, GraphQL, SOAP) adds to the difficulty. Compliance with regulations like SOC 2, HIPAA, or PCI DSS further complicates operations.
Top API Security Tools for 2025
Here are five tools designed to address these challenges:
- Jit: Focuses on vulnerability assessment and integrates with tools like OWASP ZAP and Semgrep. Best for startups due to its affordability and CI/CD integration.
- Salt Security: Excels in API discovery and runtime protection using AI/ML. Ideal for enterprises with complex needs.
- Noname Security: Offers detailed API discovery and compliance reporting. Great for large businesses but has a steep learning curve.
- Traceable AI: Combines tracing and behavioral analytics for precise anomaly detection. Effective but resource-intensive.
- 42Crunch: Works with any API gateway and cloud platform. Lacks AI features but offers consistent deployment.
Key Takeaway
Choose a tool based on your organization's size, budget, and security requirements. Smaller businesses may start with Jit, while enterprises can benefit from advanced AI-driven solutions like Salt Security or Traceable AI.
From The F5 Booth: Brian Van Lieu talks Multi-Cloud API Defense
1. Jit
Jit has earned recognition as the Best overall API security tool of 2025, thanks to its open ASPM platform tailored to tackle the unique challenges of securing APIs in multi-cloud environments. Unlike tools that aim to replace existing systems, Jit's Open Application Security Posture Management (ASPM) platform integrates seamlessly with established security tools, enhancing their capabilities.
Multi-cloud compatibility
Jit's platform is designed to work effortlessly across leading cloud providers like AWS, Azure, and Google Cloud. It integrates with popular security tools such as OWASP ZAP, Semgrep, and KICS, ensuring comprehensive API protection. What makes it stand out is its ability to secure various API types and frameworks, making it a go-to solution for organizations managing diverse technology stacks. Instead of focusing solely on runtime defense, Jit emphasizes contextual vulnerability assessment, offering insights into potential risks within multi-cloud environments.
Runtime protection
Jit redefines runtime protection by providing runtime context rather than traditional defenses. This means it evaluates whether vulnerable code is in production, exposed to the internet, or interacting with sensitive data.
"Jit's Open ASPM platform simplifies API security management by integrating with industry-leading tools like OWASP ZAP, Semgrep, and KICS to detect vulnerabilities early, offering real-time fixes, automated vulnerability management, and streamlined security protocols." – Jit
This approach helps security teams focus their resources on addressing the most pressing risks, ensuring that genuine threats to production environments are identified and mitigated.
AI/ML threat detection
Leveraging artificial intelligence and machine learning, Jit continuously monitors for unusual activity. It detects subtle anomalies, such as SQL injection attempts or data scraping activities, in real time.
"Real-time threat detection constantly scans for unusual patterns, like SQL injections or data scraping attempts, using machine learning to flag subtle anomalies. This feature helps you intercept attacks the moment they appear." – Jit
2. Salt Security
Salt Security offers a robust solution for API protection by leveraging advanced behavioral analysis to spot risks before they turn into full-blown security incidents. Its platform focuses on understanding API behavior to proactively address vulnerabilities.
Multi-cloud compatibility
Salt Security seamlessly integrates with AWS, Microsoft Azure, and Google Cloud Platform, providing a consistent layer of security across these environments. It works with your existing cloud infrastructure without requiring major changes, making it a practical choice for businesses with distributed API ecosystems. Thanks to its agentless deployment, the platform can secure APIs within minutes, whether they're running on Kubernetes, traditional virtual machines, or other containerized setups.
API discovery
One of Salt Security's standout features is its ability to automatically discover APIs. It continuously scans your multi-cloud environment to identify both documented APIs and shadow APIs that may have gone unnoticed. The platform maps API endpoints, tracks data flows, and catalogs how sensitive information is handled across your infrastructure. This is particularly useful for organizations with complex environments, such as those that have expanded through acquisitions or have multiple development teams deploying APIs independently. Once all endpoints are identified, the platform enforces strict runtime monitoring to detect and address deviations.
Runtime protection
Salt Security's runtime protection establishes a baseline of normal behavior for each API endpoint and actively monitors for any deviations that could signal malicious activity. This capability enables it to detect sophisticated threats, including zero-day attacks, that might evade traditional security tools. By analyzing factors like request frequency, payload structure, user behavior, and data access patterns, the platform can identify threats in real-time and respond effectively.
AI/ML threat detection
To enhance its runtime defenses, Salt Security employs AI-driven techniques for advanced threat detection. Its AI engine analyzes API transactions to uncover subtle attack patterns, such as business logic abuse, credential stuffing, and data exfiltration. Over time, the system learns from these interactions, improving its ability to differentiate between legitimate API usage and malicious behavior. This adaptive learning reduces false positives and ensures that genuine threats are flagged promptly, helping security teams respond faster and more accurately.
3. Noname Security
Noname Security offers a comprehensive approach to API security, emphasizing complete visibility and proactive threat detection across multi-cloud environments. Its platform is designed to provide consistent protection throughout the entire API lifecycle, from development to deployment, ensuring vulnerabilities are addressed at every stage.
Multi-cloud compatibility
Noname Security is built to work seamlessly with AWS, Microsoft Azure, and Google Cloud Platform, making it adaptable for cloud-native and hybrid setups. Whether your infrastructure relies on microservices, serverless functions, or traditional monolithic applications in containerized environments, Noname Security's platform ensures smooth integration. This multi-cloud compatibility supports its advanced API discovery and security processes.
API discovery
One of the standout features of Noname Security is its ability to automatically inventory APIs, including those that might otherwise go unnoticed. These "shadow APIs", often introduced without proper security measures, are cataloged to provide a complete view of your API ecosystem. The platform maps API specifications and authentication methods across diverse environments, offering valuable insights for organizations with fast-paced development cycles and frequent API deployments.
Runtime protection
Noname Security continuously monitors API traffic to establish behavioral patterns for each endpoint. By tracking metrics like request volumes, response times, data access patterns, and user behaviors, the platform identifies anomalies that could signal potential threats. When suspicious activity is detected, it can trigger alerts or take immediate action to block the threat. This real-time monitoring spans all connected cloud environments, ensuring consistent API protection regardless of where they are hosted.
CI/CD integration
The platform integrates directly into CI/CD pipelines, enabling security checks during both the build and deployment stages. It scans API specifications, tests endpoints for vulnerabilities, and validates security settings before APIs are released into production. This proactive approach helps development teams address security risks early, reducing the chances of deploying vulnerable APIs. Noname Security supports popular CI/CD tools and can enforce security policies as part of automated workflows.
AI/ML threat detection
Noname Security employs machine learning to analyze API traffic and uncover sophisticated attack patterns that traditional tools might miss. Its AI engine processes vast amounts of data to detect subtle threats like business logic attacks, credential abuse, and data exfiltration. By adapting to new and evolving risks, the system minimizes false positives while ensuring real threats are addressed promptly across your multi-cloud API infrastructure.
sbb-itb-bec6a7e
4. Traceable AI
Traceable AI combines tracing and behavioral analytics to secure APIs in multi-cloud environments. By using an AI-powered approach, it merges distributed tracing with behavioral analysis to establish normal patterns and quickly identify deviations. This tool stands out with its integrated tracing capabilities and precise anomaly detection.
Multi-cloud Compatibility
Traceable AI is designed to secure distributed architectures, seamlessly integrating with cloud-native, microservices, and containerized environments. It supports major platforms like AWS, Microsoft Azure, and Google Cloud Platform, as well as hybrid deployments.
API Discovery
The platform automatically maps and catalogs APIs, uncovering both documented and undocumented endpoints. By analyzing API specifications, data flows, and transactions, it creates a detailed inventory of APIs, including shadow APIs that may otherwise go unnoticed. This comprehensive mapping ensures organizations have full visibility of their API attack surface, even identifying legacy or overlooked endpoints. This detailed understanding enhances its real-time monitoring capabilities.
Runtime Protection
With continuous monitoring of API activity and user behavior, Traceable AI establishes baseline operations and swiftly blocks any anomalies that deviate from these norms.
AI/ML Threat Detection
Traceable AI leverages machine learning to define API behavior baselines, enabling it to detect unusual activity, such as unexpected user actions or traffic surges.
"We use our machine intelligence to send ONLY valid alerts - whether it's highly anomalous user behavior or an anomalous flood of incoming API calls from a foreign IP address."
The AI engine identifies a wide range of threats, including zero-day attacks, business logic abuse, OWASP Top 10 vulnerabilities, DDoS attacks, and sensitive data breaches. It continuously adapts to emerging threats with high accuracy and minimal false positives. By analyzing complete session lifecycles in real time, it detects bots early, preventing account takeovers, scraping attempts, and fraudulent activities.
Additionally, Traceable AI examines API traffic to identify the potential exposure of sensitive data, providing security severity warnings and highlighting critical vulnerabilities that demand immediate attention. This ML-driven detection capability strengthens its position as a robust solution for API security in multi-cloud environments.
5. 42Crunch
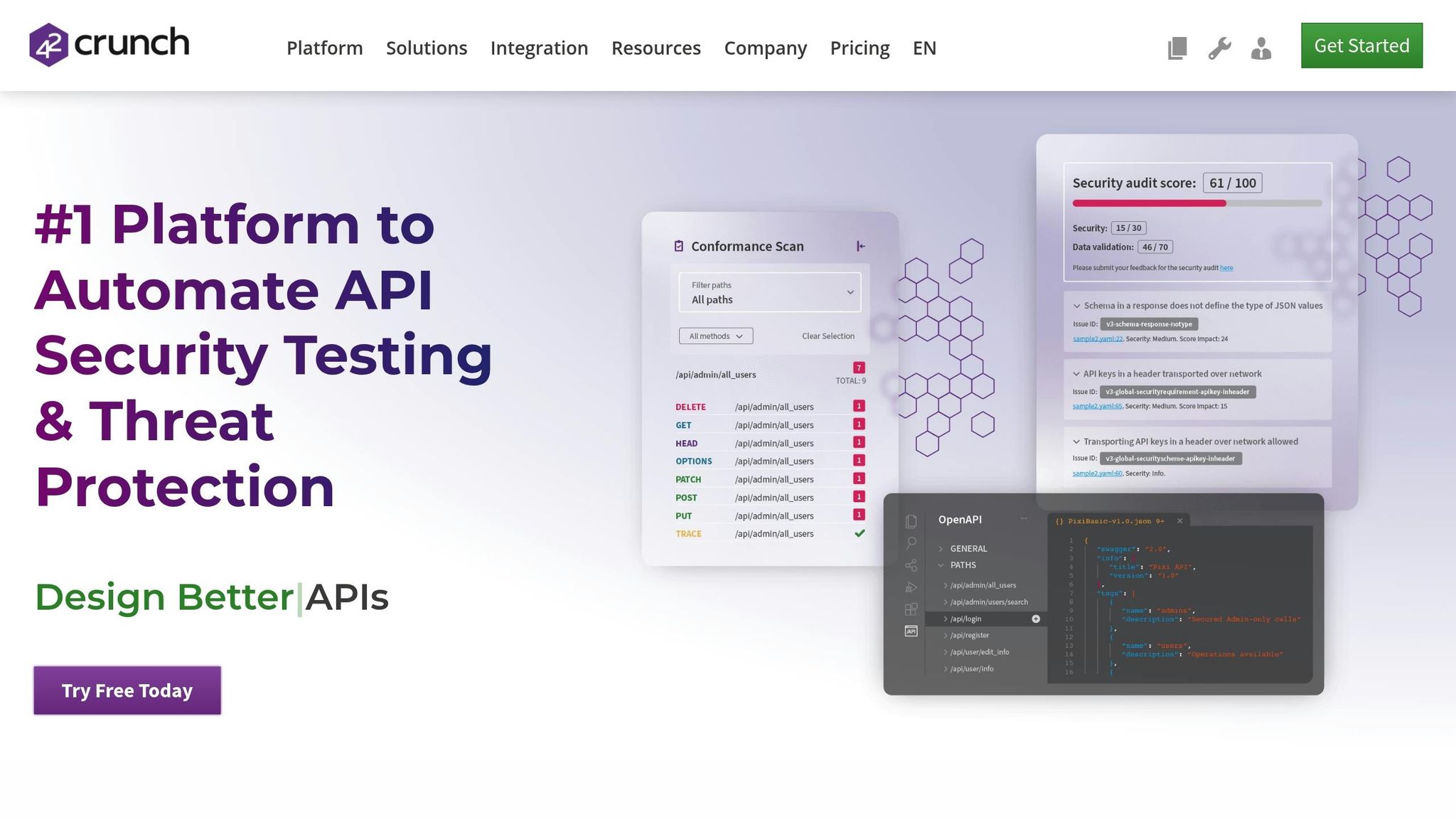
42Crunch ensures seamless integration across various cloud environments thanks to its deployment policies that work independently of specific platforms. Its standardized runtime policies are designed to operate with any API Gateway, providing consistent security no matter the cloud provider. Additionally, it supports scaling on platforms like Kubernetes, Amazon ECS, and Red Hat OpenShift. These features make 42Crunch a reliable choice for managing API security in multi-cloud setups.
Tool Comparison: Strengths and Weaknesses
When it comes to securing APIs in multi-cloud environments, each tool brings its own set of advantages and limitations. By understanding these nuances, organizations can make informed decisions tailored to their specific needs and infrastructure.
| Tool | Strengths | Weaknesses |
|---|---|---|
| Jit | Seamless CI/CD integration with automated security workflows; Thorough vulnerability scanning throughout the development process; Budget-friendly option for startups and mid-sized companies | Lacks advanced threat detection features; May need supplementary tools for complex enterprise setups; Runtime protection capabilities are still evolving |
| Salt Security | AI/ML-powered threat detection and behavioral analysis; Outstanding API discovery and inventory management; Real-time monitoring for strong runtime protection | Higher costs may deter smaller businesses; Initial setup can be complex; Requires skilled security professionals to fully utilize its potential |
| Noname Security | Exceptional API discovery for intricate multi-cloud setups; Detailed posture management and compliance reporting; Integrates well with existing security tools | Premium pricing may be a barrier; High alert volumes demand careful tuning; Steeper learning curve for teams unfamiliar with API security |
| Traceable AI | Advanced AI-driven threat detection and response; Excellent behavioral analysis and anomaly detection; Effective against sophisticated attacks | Deployment can be resource-intensive; Demands higher infrastructure capacity; Initial tuning may result in false positives |
| 42Crunch | Works across any cloud environment with platform-agnostic deployment; Standardized security policies compatible with multiple API gateways; Strong support for Kubernetes and containers | Lags behind in AI/ML capabilities compared to other tools; Manual policy setup can be time-consuming; Limited features for automated threat response |
Conclusion
Securing APIs in a multi-cloud environment calls for solutions that align with your organization's specific needs, balancing cost, complexity, and scalability. The tools discussed earlier each bring unique strengths to the table, catering to different organizational sizes and requirements.
For startups and mid-sized companies, Jit offers an affordable option with seamless CI/CD integration, making it a practical choice for those just starting to build their security framework. On the other hand, Salt Security and Traceable AI are ideal for enterprises with more complex needs. These tools leverage AI for advanced threat detection but come with higher costs and require skilled implementation. If compliance reporting is a top priority, Noname Security is a strong contender for larger enterprises, though its price and learning curve may not suit smaller organizations. Lastly, 42Crunch stands out for its compatibility across platforms and ease of deployment, though it lacks advanced AI features.
When choosing an API security tool, consider your organization’s current security maturity, budget, and future growth plans. Smaller businesses might find it easier to start with Jit and scale up as their needs evolve. Larger enterprises, however, can benefit significantly from AI-powered solutions like Salt Security or Traceable AI.
For insights into how AI is reshaping business operations and driving digital transformation, check out AI for Businesses.
FAQs
What are the key challenges of securing APIs in multi-cloud environments, and how can security tools help overcome them?
Securing APIs in multi-cloud environments can be tricky. You’re dealing with challenges like keeping security policies consistent across various cloud platforms, managing vulnerabilities that come with API versioning, and unifying authentication and authorization processes despite differing configurations.
That’s where API security tools come in handy. Tools like API gateways (e.g., AWS API Gateway, Kong, Apigee) centralize access control, enforce authentication, apply rate limiting, and maintain consistent security policies across all your cloud providers. By doing so, they simplify API management and significantly lower security risks, giving your APIs robust protection in these complex multi-cloud setups.
How do AI and machine learning improve API security tools like Salt Security and Traceable AI?
AI and machine learning are transforming API security tools, making them smarter and faster at identifying and addressing potential threats. Solutions like Salt Security and Traceable AI tap into these technologies to spot risks in real time, flag unusual behavior, and uncover vulnerabilities before they can be exploited.
Take Salt Security as an example - it uses big data along with AI and machine learning to automate threat detection, ensuring stronger and more reliable protection. Similarly, Traceable AI relies on AI-powered insights to continuously monitor APIs and guard against malicious activity. These advanced tools enable round-the-clock monitoring, early threat detection, and customized security strategies, shifting API protection from reactive to proactive.
What should organizations look for in an API security tool for multi-cloud environments?
When choosing an API security tool for a multi-cloud environment, it’s crucial to prioritize compatibility with various cloud platforms and APIs. The tool should also provide essential security features, such as authentication, access control, encryption, and real-time monitoring, to safeguard your systems effectively.
Equally important is selecting a solution that delivers centralized visibility and risk management across all cloud environments. Look for features like automated policy management, straightforward deployment, and the ability to scale with complex infrastructures. These capabilities not only strengthen your security but also streamline management, ensuring smooth operations in multi-cloud setups.